The folks at MITRE have created yet another awesome tool. CALDERA uses the ATT&CK model to simulate adversary behavior. It’s a great way to generate logs for hunting, or see how your detection stacks up. Here’s how I got it going.
I pretty much just followed along with the instructions on their github site.
- Installed a debian 9.2 VM as the Caldera server.
- Installed python 3.5, pip3, upgraded setuptools, did a git clone of the caldero repo, and did a pip -r requirements.txt.
- Installed mongodb 3.2 from source.
- Added ‘replSet = caldera’ to /etc/mongodb.conf and restarted mongodb
- Installed mono-develop with apt-get and compiled Crater with ‘buildall.bat’ on the Debian system. https://github.com/mitre/caldera-crater
- Renamed the Windows8 exe to ‘CraterMain.exe’ and dropped it in ‘caldera/dep/crater/crater’
- Started the caldera server. ‘python3 caldera/caldera/caldera.py’
Next, I configured a Windows victim.
I built a 2012R2 Domain Controller, and downloaded a free Windows10 VM from here. https://developer.microsoft.com/en-us/microsoft-edge/tools/vms/ Once one is setup, I can clone as many hosts as I want.
- Install python 3.5. I’m lazy so I set path in the installer
- Grab and install the Win64 Python 3.5 version pywin32 from here https://sourceforge.net/projects/pywin32/files/pywin32/Build%20220/
- Install VS 2015 C++ Build tools http://landinghub.visualstudio.com/visual-cpp-build-tools
- Clone the agent repo and do ‘pip install -r requirements.txt’ and ‘pip install –upgrade setuptools’ in the root of it.
- Clone MITREs py2exe repo https://github.com/mitre/caldera-py2exe
- Open the VS2015 x64 command prompt, CD into the custom py2exe and run ‘python setup.py bdist’ followed by ‘python setup.py bdist_egg’
- cd into caldera-py2exe-master\dist and run easy_install py2exe
- cd back into the agent directory\caldera_agent and run ‘make.bat’
- Copy ‘cagent.exe’ to c:\program files\cagent\
- Goto c:\program files\cagent\ and pull the config file from the caldera server https://whatever:8888/conf.yml
- Don’t forget to mod your hosts file.
- Install/start the agent with ‘cagent.exe –startup auto install’ followed by ‘cagent.exe start’
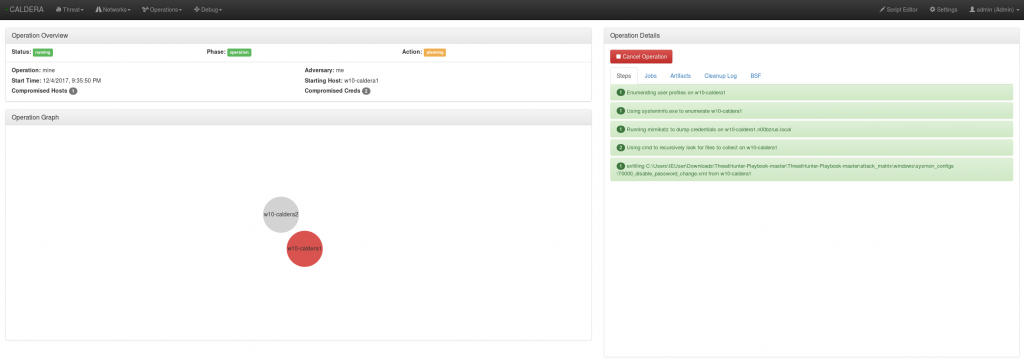
I then logged into the Caldera server with admin/caldera, created a network, and ran several test operations. It comes with a few adversary tactics built in.
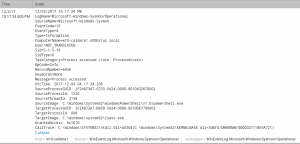
More to come on importing new TTPs, expanding on the ATT&CK model, and writing Sysmon configs.
0 Comments