Here’s how to generate custom certs and perform a MITM + SSL decryption with bettercap or Squid.
MITM with Bettercap.
Create a private key, CSR, and Certificate.
openssl genrsa -out mitm.key 2048 openssl req -new -key mitm.key -out mitm.csr openssl x509 -req -days 3652 -in mitm.csr -signkey mitm.key -out mitm.crt
Convert to pem.
openssl pkcs12 -export -in mitm.crt -inkey mitm.key -out mitm.p12 openssl pkcs12 -in mitm.p12 -nodes -out mitm.pem
Convert to der for the client.
openssl x509 -in mitm.pem -outform DER -out mitm.der
Import the der certificate into the Trusted Root Certificate Store of your targets.
Export the private key out to pem format so you can view decrypted packets in Wireshark. Or just use the mitm.pem from above. Sometimes it works, sometimes it doesn’t.
openssl pkcs12 -nodes -in mitm.p12 -out mitmkey.pem -nocerts
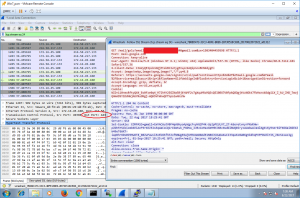
In Wireshark, go to Edit/Preferences/Protocols/SSL, and Edit RSA keys. Enter it like so.
0.0.0.0 / 443 / http / path_to_pem_file
Tshark:
tshark -i eth0 -V -x -o "ssl.desegment_ssl_records: TRUE" -o "ssl.desegment_ssl_application_data: TRUE" -o "ssl.keys_list:0.0.0.0,443,http,mitm.pem" -f "host 172.16.45.100 and tcp port 443" -z "follow,ssl,ascii,1"
Run the MITM.
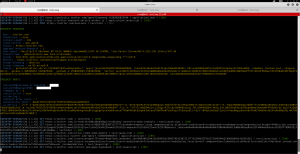
bettercap --proxy-pem mitm.pem --proxy-https -T 172.16.45.100 -P POST -X -O out.log
MITM between Squid and the Gateway:
Did a default “apt-get install squid3” and a basic “forward all” config for testing. You can use the “mitm.der” cert from earlier in your Client’s Trusted Root Store, and run bettercap with Squid as the target.
bettercap --proxy-pem mitm.pem --proxy-https -T 172.16.45.3 -P POST -X -O squidout.log
The steps for decrypting PCAP are the same as above and you already have the mitmkey.pem (private key) cert in Wireshark.
Squid Install for SSL Decryption:
A little bit more complicated. First create a private key, CSR, and Certificate.
openssl genrsa -out squid.key 2048 openssl req -new -key squid.key -out squid.csr openssl x509 -req -days 3652 -in squid.csr -signkey squid.key -out squid.crt
Convert to pem.
openssl pkcs12 -export -in squid.crt -inkey squid.key -out squid.p12 openssl pkcs12 -in squid.p12 -nodes -out squid.pem
Convert to der for the client.
openssl x509 -in squid.pem -outform DER -out squid.der
Compile Squid with the following options and use the config below to set it up as a MITM.
./configure --with-openssl --enable-ssl-crtd
Squid.conf https://raw.githubusercontent.com/mattclemons/squid/master/squid.conf
You should be able to see traffic in the squid logs.
Decrypting between Squid and the Client:
I read that “Due to the “generate-host-certificates” option in the config, Squid keeps public and private keys in this directory “/var/squid/lib/ssl_db/certs.”” I tried pulling the private keys out of the pem files and then importing them into Wireshark.
Check certificates public and private keys.
cd /var/squid/lib/ssl_db/certs for file in *.pem; do openssl rsa -in $file -check; done for file in *.pem; do openssl x509 -in $file -text -noout; done
Extract the private keys in pem format for Wireshark.
for file in *.pem; do openssl rsa -in $file -out $file.key.pem; done
Importing into Wireshark was a horrible process. I was able to see traffic from the Client to Squid, but it’s not as interesting as from Squid to the Internet.
Certificate Pinning:
MITM won’t work with HPKP. With the latest versions of top browsers, sites like twitter.com, microsoft.com, and certain banking websites have to be bypassed. Applications like Dropbox, Apple and Android App Stores have to be excluded from decryption. Check the links below for more information.
https://docs.diladele.com/faq/squid/sslbump_exlusions/apple_app_store.html
https://projects.dm.id.lv/Public-Key-Pins_test#Browser_compatibility_test
0 Comments