There are a number of things needed to stop ARP poisoning properly in a Cisco environment.
- DHCP snooping
- Trusted ports
- Dynamic ARP inspection
- A filter for static IPs
DHCP snooping prevents rogue DHCP servers and is the groundwork for all this. It builds a database of bindings and specifies where replies can come from. A trusted port is either where the DHCP server resides, or uplinks/trunks to other switches that relay DHCP traffic. If DHCP ACKs are received on an untrusted port, it gets disabled.
Dynamic ARP inspection uses the snooping database and the ACL to ensure MAC addresses map to the correct IPs on the port they’re plugged into. If someone tries to poison the ARP cache, traffic gets dropped and/or the port is disabled. Trusted ports are needed for uplinks/trunks. If there are static hosts on the network, an access list needs to be built because they wont get added to the database through DHCP.
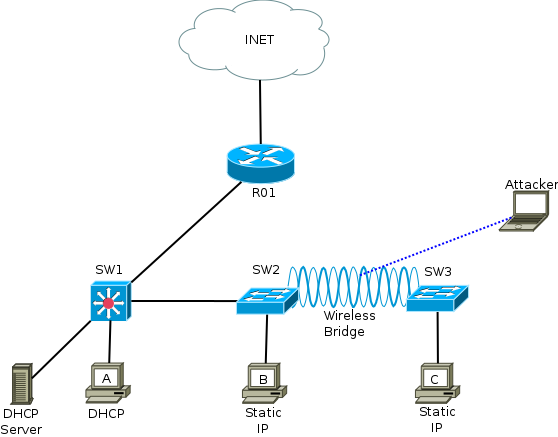
Here’s my test network.
- Router = 10.3.3.1
- DHCP = 10.3.3.20
- HostA = 10.3.3.123 (DHCP)
- HostB = 10.3.3.3 (static)
- HostC = 10.3.3.4 (static)
- Attacker = 10.3.3.44 (DHCP) on WiFi
The router is connected to g0/1 on SW1.
The DHCP server is connected to g0/2.
HostA is connected to g0/5
Port g0/3 is the dumb uplink between SW1 and SW2.
There’s a wireless bridge between SW2 and SW3.
Below I trust the port that the DHCP server is on plus the uplink to SW2. Then enable DHCP Snooping globally and for VLAN 1. I disable option 82, because there’s no relay, and then verify.
int g0/2 descr DHCP_SERVER ip dhcp snooping trust ! int g0/3 descr UPLINK_TO_SW2 ip dhcp snooping trust ! exit ip dhcp snooping ip dhcp snooping vlan 1 no ip dhcp snooping information option ! end
sh ip dhcp snooping Switch DHCP snooping is enabled DHCP snooping is configured on following VLANs: 1 DHCP snooping is operational on following VLANs: 1 DHCP snooping is configured on the following L3 Interfaces: Insertion of option 82 is disabled circuit-id default format: vlan-mod-port remote-id: muah.haah.haah (MAC) Option 82 on untrusted port is not allowed Verification of hwaddr field is enabled Verification of giaddr field is enabled DHCP snooping trust/rate is configured on the following Interfaces: Interface Trusted Allow option Rate limit (pps) ----------------------- ------- ------------ ---------------- g0/2 yes yes unlimited Custom circuit-ids: g0/3 yes yes unlimited
sh ip dhcp snooping binding MacAddress IpAddress Lease(sec) Type VLAN Interface ------------------ --------------- ---------- ------------- ---- -------------------- HA:HA:HA:HA:HA:HA 10.3.3.123 5853 dhcp-snooping 1 g0/5 MU:HA:HA:HA:HA:HA 10.3.3.44 6974 dhcp-snooping 1 g0/3
debug ip dhcp snooping event debug ip dhcp server packet
Next I build the static ARP access list.
arp access-list STATIC_ARP permit ip host 10.3.3.3 mac host aaaa.bbbb.cccc permit ip host 10.3.3.4 mac host bbbb.cccc.dddd
Trust the uplink to SW2 and the DHCP server port, apply the access list, and enable ARP inspection on VLAN 1.
int g0/2 ip arp inspection trust ! int g0/3 ip arp inspection trust ! ip arp inspection filter STATIC_ARP vlan 1 ip arp inspection vlan 1
This can also be achieved through IP source binding, but the ACL is easier to manage IMO.
ip source binding aaaa.bbbb.cccc vlan 1 10.3.3.3 interface g0/3 ip source binding bbbb.cccc.dddd vlan 1 10.3.3.4 interface g0/5
When I try to arp spoof with any tool, the traffic is dropped and nothing happens to the target. The attacker can still access the network, and the following logs are generated.
%SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Gi0/3, vlan 1.([asdf.asdf.asdf/10.3.3.1/fdsa.fdsa.fdsa/10.3.3.5/17:50:13 CST Wed Sep 27 2017]) %SW_DAI-4-DHCP_SNOOPING_DENY: 1 Invalid ARPs (Res) on Gi0/3, vlan 1.([asdf.asdf.asdf/10.3.3.1/fdsa.fdsa.fdsa/10.3.3.5/17:50:13 CST Wed Sep 27 2017])
However, scanning the subnet for targets with tools like bettercap puts the port in err-disabled state.
SW1#sh int g0/3 status Port Name Status Vlan Duplex Speed Type g0/3 err-disabled 1 auto auto 100/1000BaseTX
This is bad because other systems use that uplink. By default there is a limit of 15 ARP packets per second on a port. I disable it like so.
int g0/3 ip arp inspection limit none
To enable timing to bring the port(s) back up run the following.
SW1(config)#errdisable recovery cause arp-inspection SW1(config)#errdisable recovery interval 30 %PM-4-ERR_RECOVER: Attempting to recover from arp-inspection err-disable state on g0/3 %LINK-3-UPDOWN: Interface g0/3, changed state to up %LINEPROTO-5-UPDOWN: Line protocol on Interface g0/3, changed state to up SW1(config)#do sh int g0/3 status Port Name Status Vlan Duplex Speed Type g0/3 connected 1 a-full a-1000 100/1000BaseTX
More validation.
SW1#sh ip arp inspection statistics vlan 1 Vlan Forwarded Dropped DHCP Drops ACL Drops ---- --------- ------- ---------- --------- 1 14543 562 562 0 Vlan DHCP Permits ACL Permits Probe Permits Source MAC Failures ---- ------------ ----------- ------------- ------------------- 1 316 6554 0 0 Vlan Dest MAC Failures IP Validation Failures Invalid Protocol Data ---- ----------------- ---------------------- --------------------- 1 0 0 0
0 Comments